Ransomware continues to be a major concern, affecting a wide range of industries. According to the 2024 Data Breach Investigations Report by Verizon, ransomware remains a top threat for 92% of industries, with nearly one-third of all data breaches involving ransomware or other forms of extortion. What’s even more concerning is how sophisticated these ransomware operations have become, functioning much like legitimate businesses with their own marketing teams and development departments. These groups have even started offering RaaS (Ransomware as a Service), making it easier for cybercriminals to launch attacks. It’s almost genius, except it’s one of the most dangerous cybersecurity threats out there.
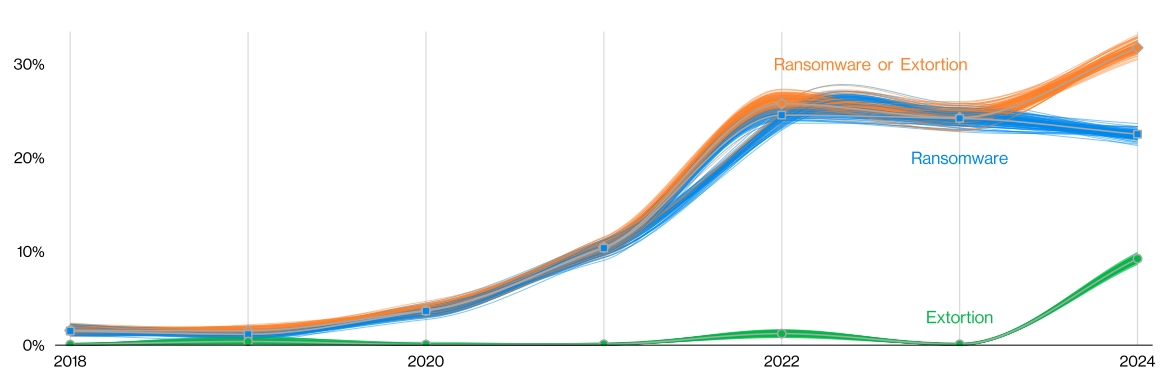
Ransomware and Extortion breaches over time (Verizon’s 2024 Data Breach Investigations Report)
Breaches related to third-party vendors or supply chain vulnerabilities are also on the rise. This year, 15% of all breaches were linked to partner infrastructure or supply chain issues, representing a 68% increase from the previous year. Much of this increase is due to the use of zero-day exploits in ransomware and extortion attacks.
Before diving into practical steps to protect your organization from ransomware, let’s first understand what ransomware is and why it poses such a significant threat to business cybersecurity. Then, we’ll explore 10 actionable strategies to help safeguard your data against these attacks.
What is ransomware?
Ransomware is a type of malicious software (malware) designed to extort money from victims by holding their data hostage. Essentially, ransomware encrypts the victim's files or locks them out of their system, demanding payment in exchange for the decryption key or access to the system.
Ransomware typically enters a system through social engineering tactics, such as phishing emails, or by exploiting vulnerabilities in outdated software or weak security measures. Once on the victim's system, it encrypts the files or locks the user out. The attacker then demands payment, often with a deadline, threatening to delete or permanently encrypt the files if the ransom isn't paid.
Data stolen through ransomware is often sold on the dark web. Paying the ransom doesn’t guarantee its safe return—you are, after all, dealing with criminals motivated by money, not a good conscience.

How does ransomware get into a network?
Ransomware can enter a system through a variety of means, including:
- Phishing emails: This common tactic involves tricking individuals into giving up sensitive information through emails that appear to be from legitimate sources. Ransomware often spreads through phishing emails that contain malicious attachments or links to infected websites.
- Direct install: Threat actors use their existing system access to install ransomware directly. This can occur when attackers have already compromised the system through other means, such as stolen credentials or previous breaches.
- Web applications: Exploiting vulnerabilities in web applications is another frequent method. Attackers target web applications to inject malware into systems.
- Desktop sharing software: Threat actors gain entry by exploiting vulnerabilities in desktop sharing software, which allows them to access and install ransomware on the system.
- Software vulnerabilities: Attackers exploit weaknesses in an organization's systems, applications, or network to gain access. This includes vulnerabilities in VPNs and software updates.
- Botnets: A network of infected computers or devices that can be controlled remotely by an attacker to carry out various malicious activities, including ransomware attacks.

What happens when a system is infected with ransomware?
Imagine someone breaking into your house and locking all your valuables in a safe that only they can open. That's essentially what happens when a system is infected with ransomware.
When ransomware infects a system, it encrypts some or all of an organization’s files and documents, making them inaccessible. The cybercriminal behind the attack then demands payment for the data’s release. This data can include everything from sensitive customer data and financial details to business secrets and marketing strategies. The impact is immediate and severe, disrupting business operations and putting sensitive information at risk.

Can ransomware be removed without paying the ransom?
Paying ransom to criminals, in any case, is discouraged. When a ransom is requested, it is crucial to contact relevant authorities first.
In some cases, ransomware removal may be possible without paying the ransom. This depends on the type of ransomware and how it was installed on the system. Attempting to remove ransomware without the proper knowledge and tools can lead to further damage to the system and potentially make the encrypted files unrecoverable.
Organizations should have a robust incident response plan that includes steps for ransomware removal and recovery. This plan should involve isolating the infected systems, identifying the type of ransomware, and using decryption tools if available. Regular backups and a good disaster recovery plan can also mitigate the impact of a ransomware attack.
Further reading: How to create a strong data loss prevention policy (a step-by-step plan)
10 best practices for ransomware prevention
Preventing ransomware attacks might seem daunting, but with the right approach, it’s very manageable. Let’s break down some easy steps your organization can take to stay safe:
Keep software up-to-date
Regular updates: Make sure all your software, from your operating system to your security tools, is always updated. Hackers love finding weaknesses in old software, so keeping everything current helps close those gaps. Automate your updates to make this even easier.
Use strong passwords and multi-factor authentication (MFA)
Complex passwords: Encourage everyone in your organization to use strong, unique passwords, and make sure to change passwords regularly.
Multi-factor authentication: Add an extra layer of security by using MFA. This means even if someone gets your password, they still need a second form of verification, like a code sent to your phone.
Regularly backup data
Frequent backups: Regularly back up all your important data and store copies in a secure, offline location. This way, if ransomware strikes, you won’t lose everything and won’t need to pay a ransom to get your data back.
Test restores: Occasionally test your backups to make sure you can actually recover your data. It’s better to know now if something isn’t working right.

Employee training and awareness
Security training: Regularly educate your employees on how keep your organization’s data safe, including how to spot phishing emails and other cyber threats. The more they know, the safer your organization will be.
Monitor employee behavior: Whether it’s restricting data transfers, controlling email attachments, or monitoring cloud storage usage, set up policies that ensure that your data handling practices align with security best practices. Test your team with simulated phishing emails to see how they handle real-life scenarios. This can help improve their responses and awareness.
Implement robust endpoint protection
Antivirus and anti-malware: Use advanced antivirus and anti-malware software on all devices. Keep this software updated so it can catch the latest threats.
Endpoint detection and response: Use data loss prevention (DLP) tools that give you real-time visibility into what’s happening on your network, including device control features that restrict the use of removable storage devices and other peripherals. This prevents malware from being introduced to your network via external devices.
Network segmentation and access controls
Segment your network: Divide your network into sections to contain any potential damage. If one part gets infected, it won’t spread everywhere.
Access controls: Only give access to sensitive data and systems to people who really need it. The fewer people with access, the lower the risk. Implement the Zero Trust Approach for maximum protection.
Secure remote access
VPNs and secure Access: Use VPNs and secure remote access tools for anyone connecting from outside the office. Make sure these tools are set up correctly and kept up-to-date.
Desktop sharing software: Limit who can use desktop sharing software and monitor its use to prevent unauthorized access.
Data encryption
Ecrypt sensitive data: Make sure to encrypt sensitive data, ensuring that even if ransomware encrypts your files, the data remains secure and inaccessible to attackers. This adds an extra layer of security, making it difficult for cybercriminals to leverage stolen data, making it less lucrative for them.

Implement data loss prevention (DLP) solutions
DLP tools: Use DLP software to monitor and control data movement in your network in realtime. This helps in quickly identifying and responding to suspicious behavior, such as unauthorized data access or large-scale data transfers that could indicate a ransomware attack.
Anomaly detection: Advanced DLP tools can detect unusual data access patterns, helping you catch potential ransomware attacks early.

Incident Response Planning
Response plan: Have a clear plan in place for what to do if ransomware strikes. This should include steps for isolating affected systems, notifying key people, and recovering data.
Further reading: Insider risk management strategies for mid-size businesses
What are the consequences of a ransomware attack?
The most obvious consequence of a ransomware attack is the loss of access to critical data and systems, significantly interfering with business operations and leading to financial losses. In some cases, organizations may be forced to pay the ransom to regain access to their files, which can be costly and does not guarantee the safe return of the encrypted data. Whether or not the ransom is paid, the risk of sensitive data being leaked is significant.
Successful ransomware attacks can result in:
- Downtime: When systems are encrypted or blocked, they may be unusable until the ransom is paid or the data recovered. That can lead to significant downtime for an organization while it tries to recover. This downtime can be particularly costly for businesses that rely on technology to conduct their operations.
- Data loss: Ransomware attacks can result in the loss of critical data and sensitive information, including customer data, financial records, and confidential business information. If the victim organization does not have a backup of the encrypted data, the loss of that data can be permanent.
- Regulatory fines: Many industries have regulations that require organizations to protect customer data. If data is compromised in a ransomware attack, the organization face fines and penalties under those regulations. For example, TISAX for automotive industry, HIPAA in healthcare, and NIS2 and GDPR for, well, almost everybody.
- Reputational damage: If sensitive customer data gets stolen and/or leaked through any kind of cybersecurity attack, the reputation of the company or organization can suffer. This damage can also be difficult to fix, especially if the organization is perceived as having been negligent in their approach to cybersecurity.
- Financial losses: Financial losses following a ransomware attack can come from remediation costs, such as data recovery and system restoration, as well as the costs of downtime, lost productivity, less business due to reputation damage, regulatory fines, legal fees, and ransom payments.

The CDK Global outage
In July 2024, CDK Global, a major player in the software industry, became the target of a two-week ransomware attack. This cyber assault caused significant disruption for thousands of car dealerships that rely on their platform, affecting an estimated 15,000 auto dealer locations throughout North America. Dealerships faced operational challenges such as being unable to access dealer management systems, experiencing interruptions in tracking and ordering car parts, and encountering difficulties in executing new sales and providing financing. Furthermore, they struggled with scheduling service appointments and managing inventory. Beyond the operational chaos, the ransomware group's breach of sensitive customer and business data presents a serious threat.
Ultimately, CDK is reported to have transferred 387 Bitcoin (around $25 million) to BlackSuit’s cryptocurrency account.
How Safetica’s DLP protects your organization against ransomware
Safetica’s DLP software provides an essential line of defense against ransomware. Here’s how:
![]() Real-Time Monitoring: Safetica continuously monitors data activity within your network, spotting and alerting you to any suspicious behavior that could signal a ransomware attack.
Real-Time Monitoring: Safetica continuously monitors data activity within your network, spotting and alerting you to any suspicious behavior that could signal a ransomware attack.
![]() User Behavior Analytics: By analyzing patterns in user behavior, Safetica can detect anomalies and potential threats early, allowing for proactive measures to stop ransomware in its tracks.
User Behavior Analytics: By analyzing patterns in user behavior, Safetica can detect anomalies and potential threats early, allowing for proactive measures to stop ransomware in its tracks.
![]() Endpoint Protection: Safetica’s robust endpoint protection features prevent unauthorized software from running on your systems, reducing the risk of malware infections.
Endpoint Protection: Safetica’s robust endpoint protection features prevent unauthorized software from running on your systems, reducing the risk of malware infections.
![]() Automated Encryption: Safetica automatically encrypts sensitive data, ensuring that even if ransomware manages to get through, your critical information remains secure and inaccessible to attackers.
Automated Encryption: Safetica automatically encrypts sensitive data, ensuring that even if ransomware manages to get through, your critical information remains secure and inaccessible to attackers.
![]() Policy Enforcement: With Safetica, you can enforce strict security policies that control data access and movement, minimizing the chances of data falling into the wrong hands.
Policy Enforcement: With Safetica, you can enforce strict security policies that control data access and movement, minimizing the chances of data falling into the wrong hands.
Next articles

Hidden Data Everywhere: Why It’s Important to Have Complete Visibility for Data Security
Modern work creates blind spots across shadow IT, AI tools, personal devices, and third-party services. This article explains why visibility is essential for effective data discovery and stronger data protection.








