Discover and secure all forms of sensitive data
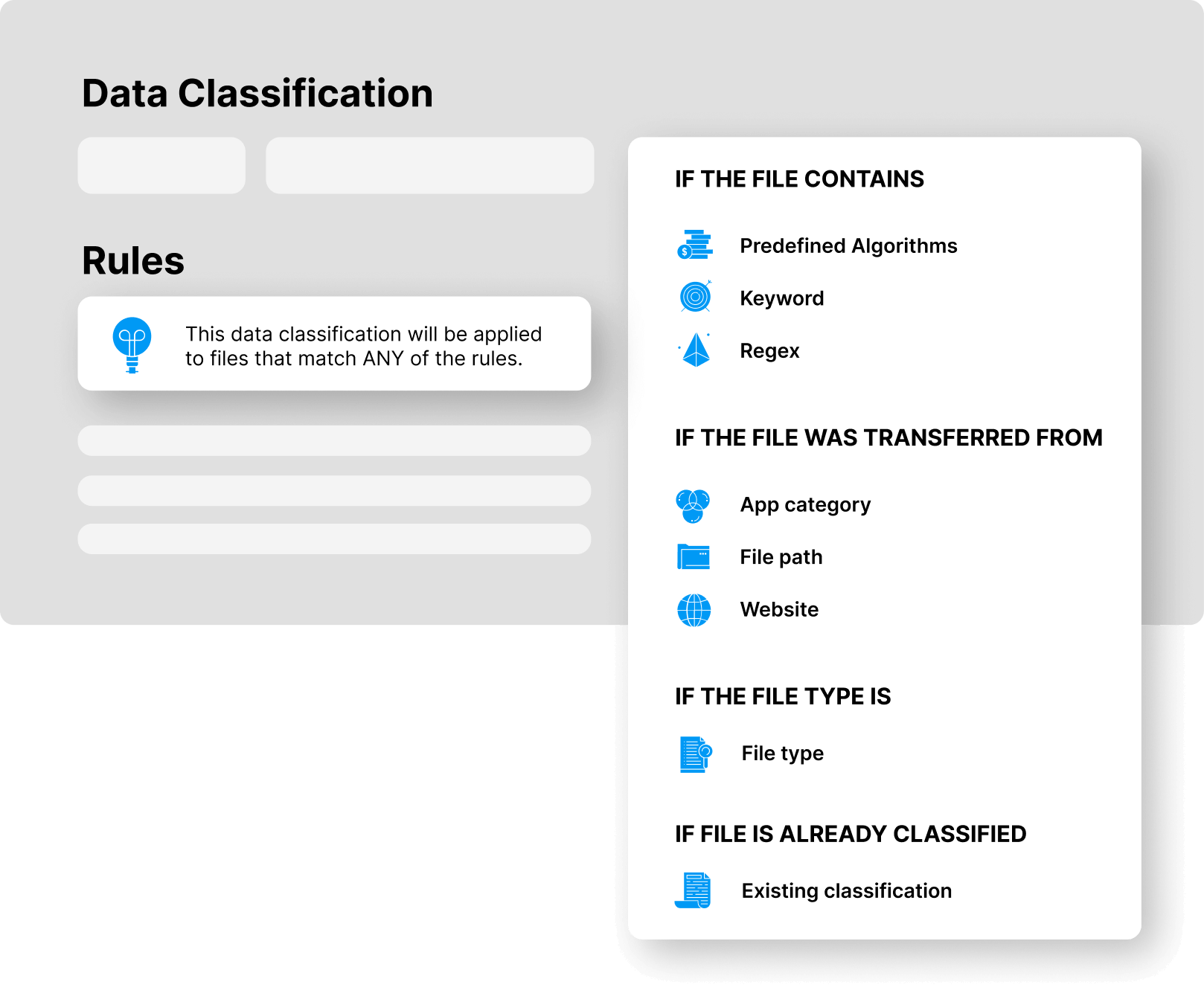
With Safetica Unified Classification, you can detect and protect data based on content, origin, file type, and even third-party classifications.
Data at rest
Safetica can search for sensitive files in selected folders on endpoints and in network shares.
Data in motion
Safetica can classify files directly during user operations, such as exports, uploads and downloads, opening files, copying files to a different path, uploading files via web browsers, sending files via email or IM apps, and others.
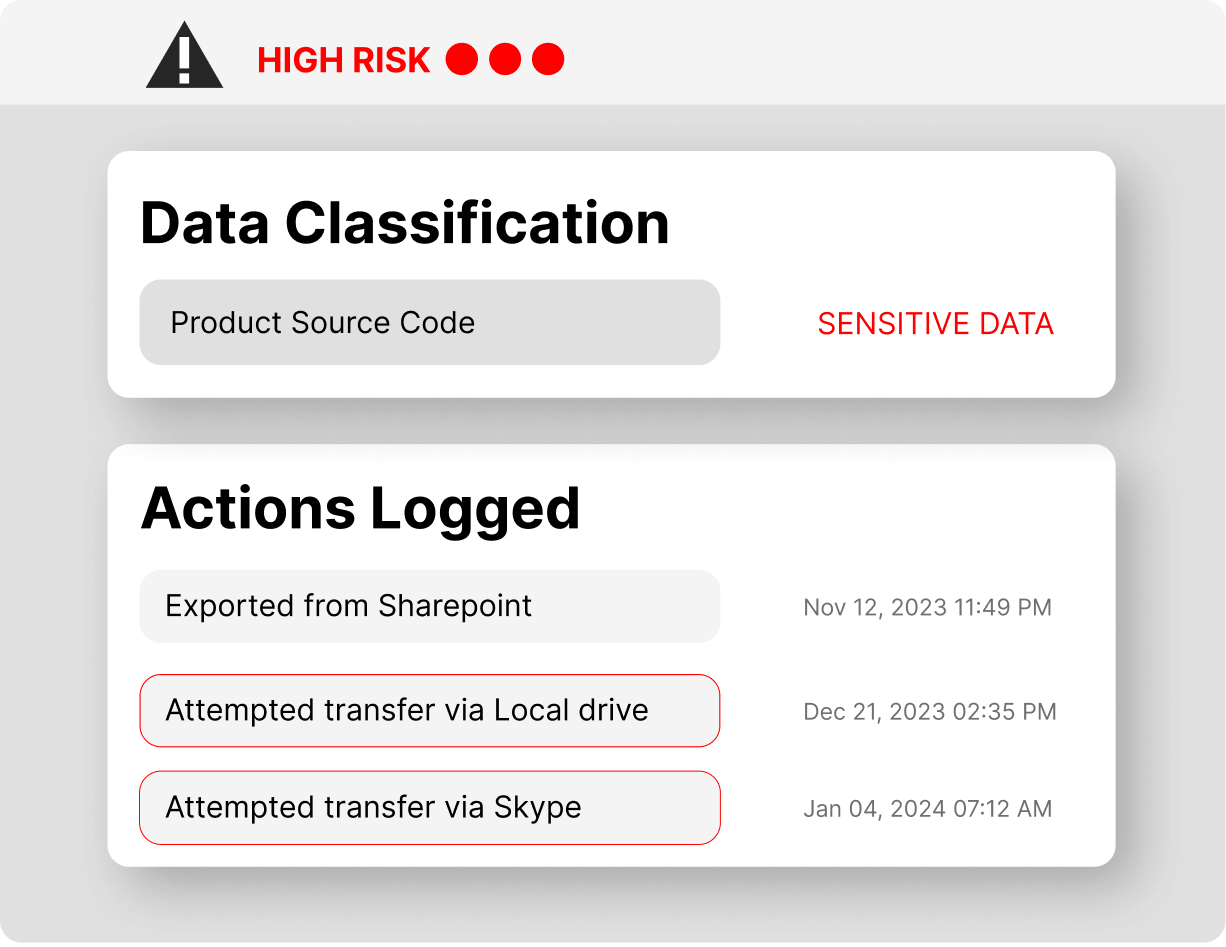
Detect insider threats, monitor risks, and mitigate them based on behavioral context
- Identify and assess employees at high risk (including those leaving, facing layoffs, working remotely, or contractors) and provide guidance to modify their behavior to prevent potential incidents.
- Uncover and eliminate undesired or redundant applications, hardware, or peripherals (known as Shadow IT) within your system.
Prevent data leakage to cloud storage and secure data in the cloud
- Establish seamless integration with Microsoft 365.
- Monitor and conduct audits of file uploads and downloads to cloud storage platforms.
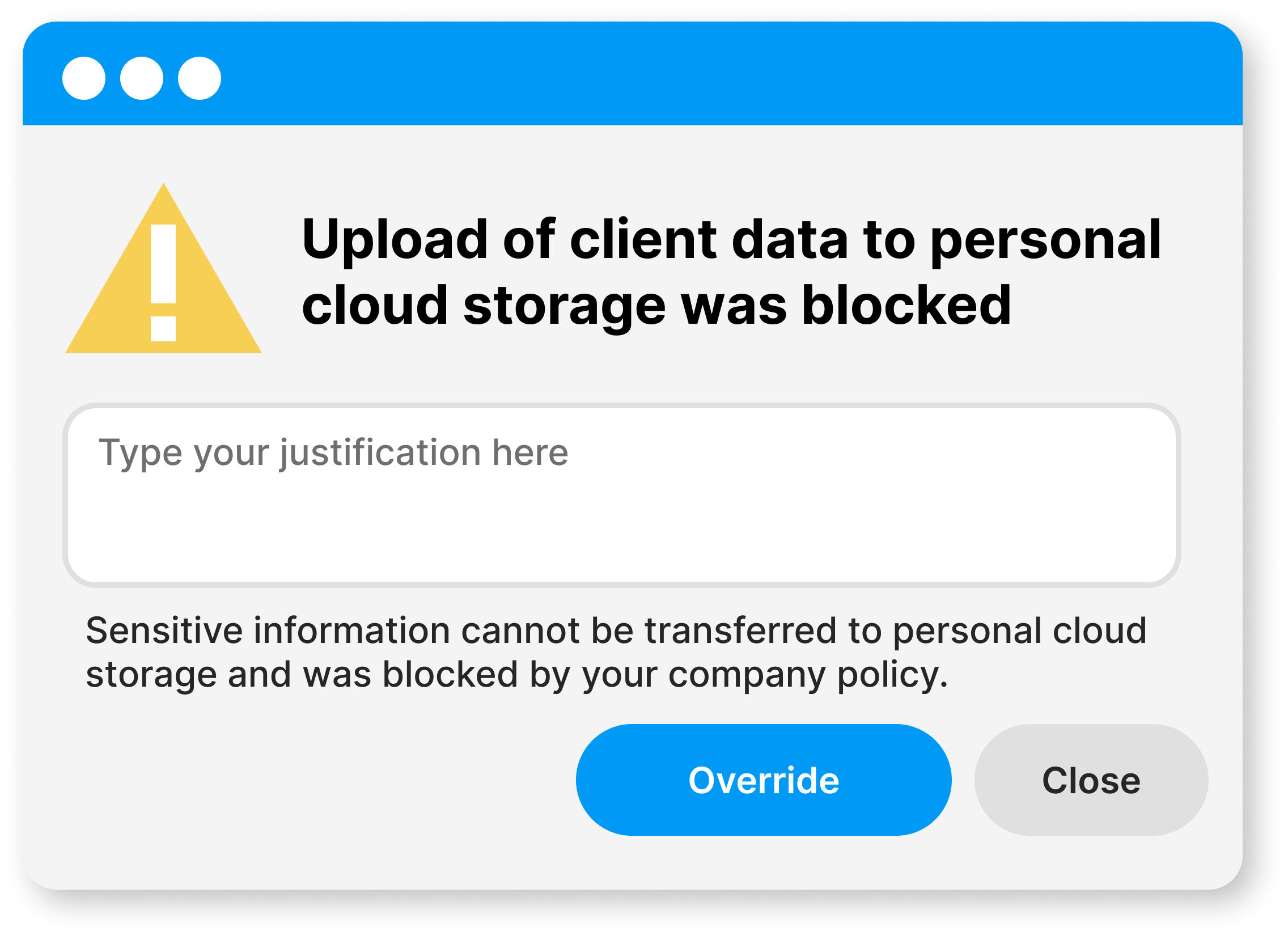
- Implement measures to prohibit the upload of sensitive files to remote cloud storage and cloud email services.
Safetica covers key data security solutions

Data Discovery and Classification
Discover your sensitive data, keep it in the spotlight and never let it out of your sight, no matter where it is stored or transferred.
more information
Data Loss Prevention
Protect confidential data from being shared with unauthorized parties. Manage your company data flow easily from one place.
more information

Insider Risk Management
Detect insider threats and early mitigate risk to your sensitive data. Timely reaction is key for efficient protection.
more information

Cloud Data Protection
Prevent the mishandling of data in corporate cloud apps, ensuring it doesn't get shared with unauthorized users
more information
Highly-rated by security admins for its product capabilities
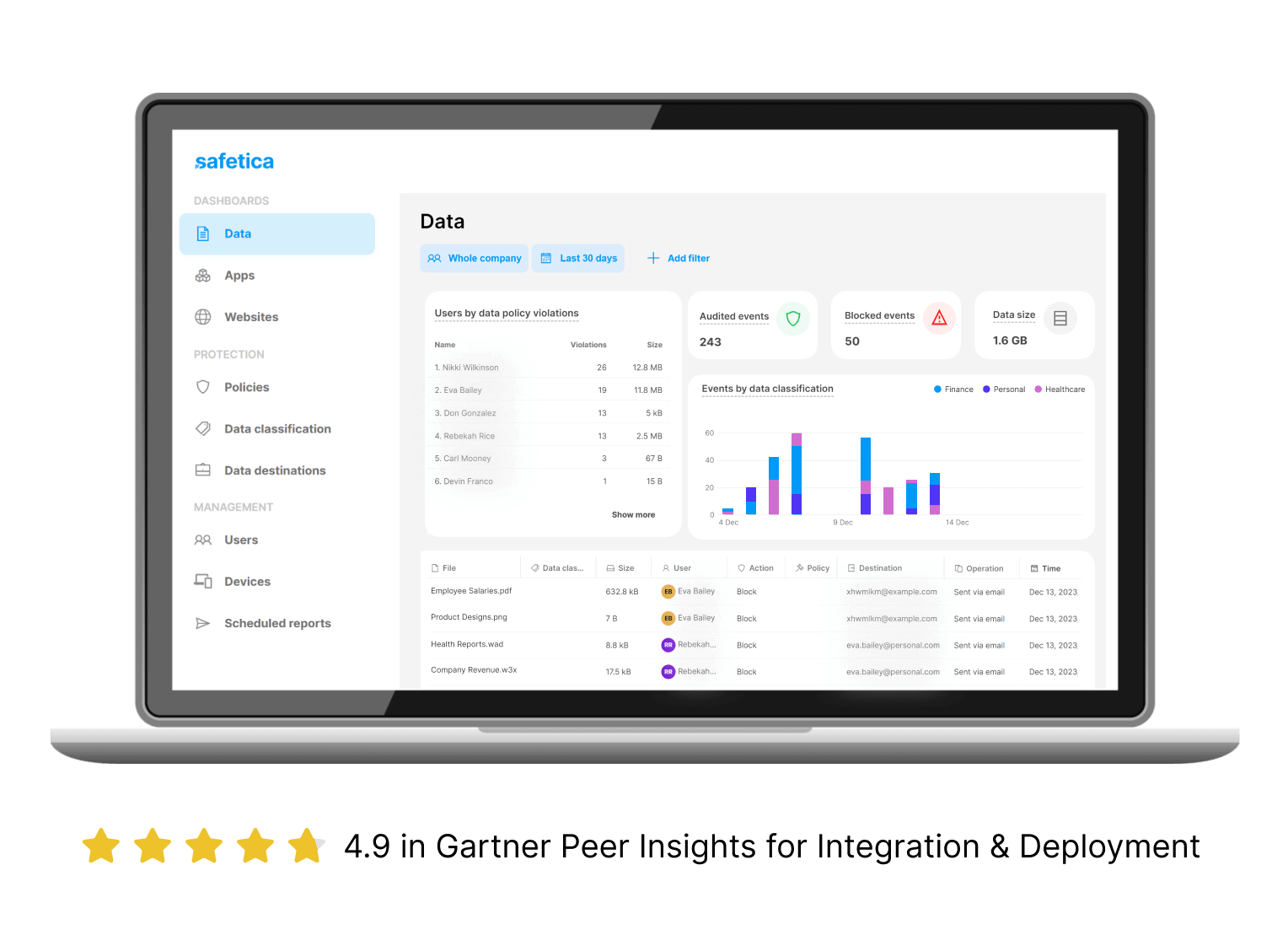
Intuitive User Interface
Our Safetica console was designed with the user in mind. Navigate effortlessly through the system, empowering users to take control of their data security without extensive training.
Simplified Deployment Process
Flexible deployment options to businesses, with on-premise installation for maximum control and security, or cloud-based hosting for greater flexibility and scalability. You can count on our industry-leading partner and vendor support throughout the process.
Protection on Day One
Equipped with ready-to-use policies, allowing rapid implementation. Immediately and automatically detect and log incidents involving sensitive data, block risky applications and websites, and initiate universal monitoring.
Seamless integration into your existing ecosystems
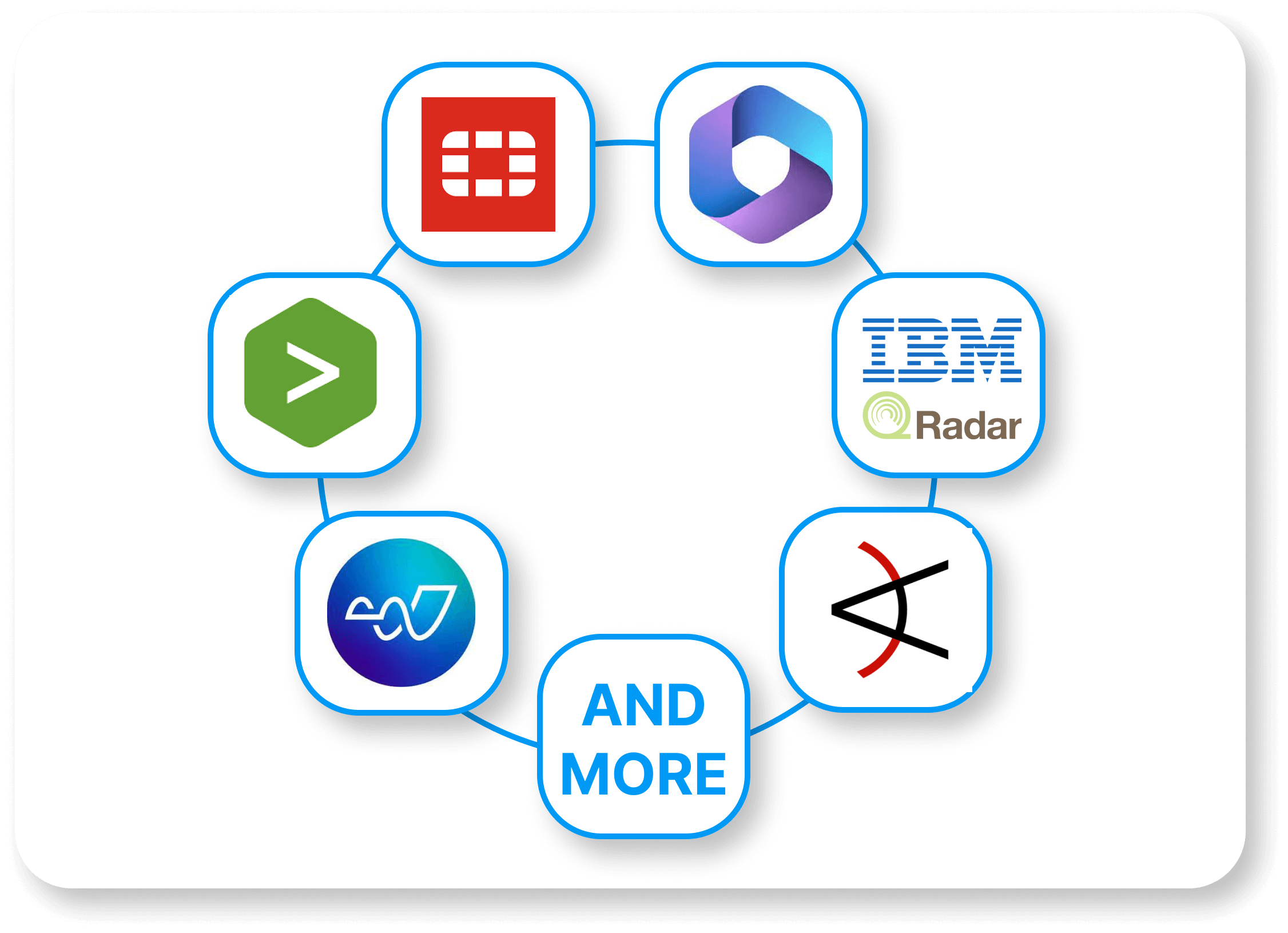
A comprehensive solution seamlessly integrates with existing security systems to safeguard enterprise environments. Data is protected across all endpoints, devices, major operating systems (Windows, macOS), and cloud environments, including perimeters and internal zones.
Native integration with Microsoft 365 and Fortinet network appliances enhances control over unknown devices, establishing a strong endpoint-to-network security framework.
Audited incidents and logs can be automatically forwarded to SIEM solutions such as Splunk, IBM QRadar, LogRhythm, or ArcSight for deeper investigation. Additionally, REST API facilitates data transfer to tools like Power BI or Tableau for advanced analysis.
One Product. Three Choices.

Detect sensitive information and security risks
Gain visibility of sensitive data flow and classify your data. Get security & regulatory audit reports.

Eliminate the risk of losing sensitive information
Secure your sensitive data with an integrated Data Loss Prevention (DLP) and Insider Risk Management solution

Protect your assets in complex environments
Optimize your product and account management and extend your data retention.
What our customers say about Safetica
Do you want more information?
Safetica Features
Find out more detailed information about Safetica
Download datasheet
Get all the use cases, key benefits and more about Safetica
Technical requirements
Technical specifications and hardware requirements for Safetica