What is Data Loss?
Data loss can occur any time your sensitive data is accidentally or intentionally shared: an email with sensitive materials gets forwarded to a competitor, a laptop with company database gets stolen or an employee walks away with comprehensive client lists.
When sensitive data is lost or stolen, a company’s reputation, competitive advantage and profitability all suffer. There can also be legal liabilities to be faced.

Safetica covers today’s most critical data security scenarios
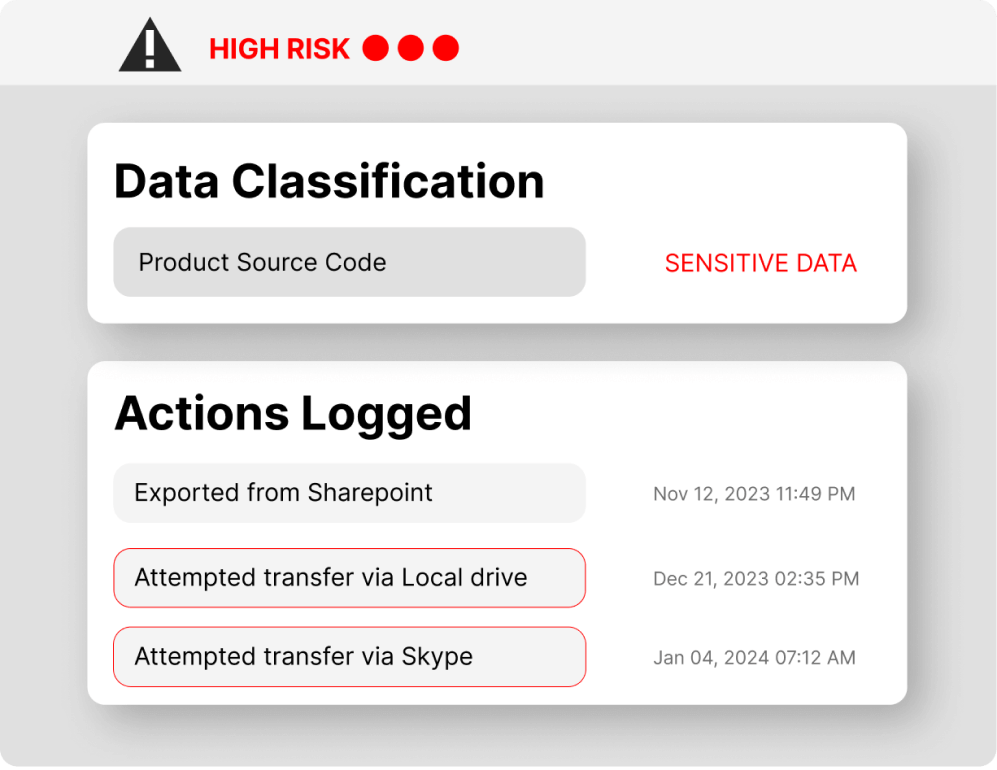
Gain data visibility and discover sensitive data
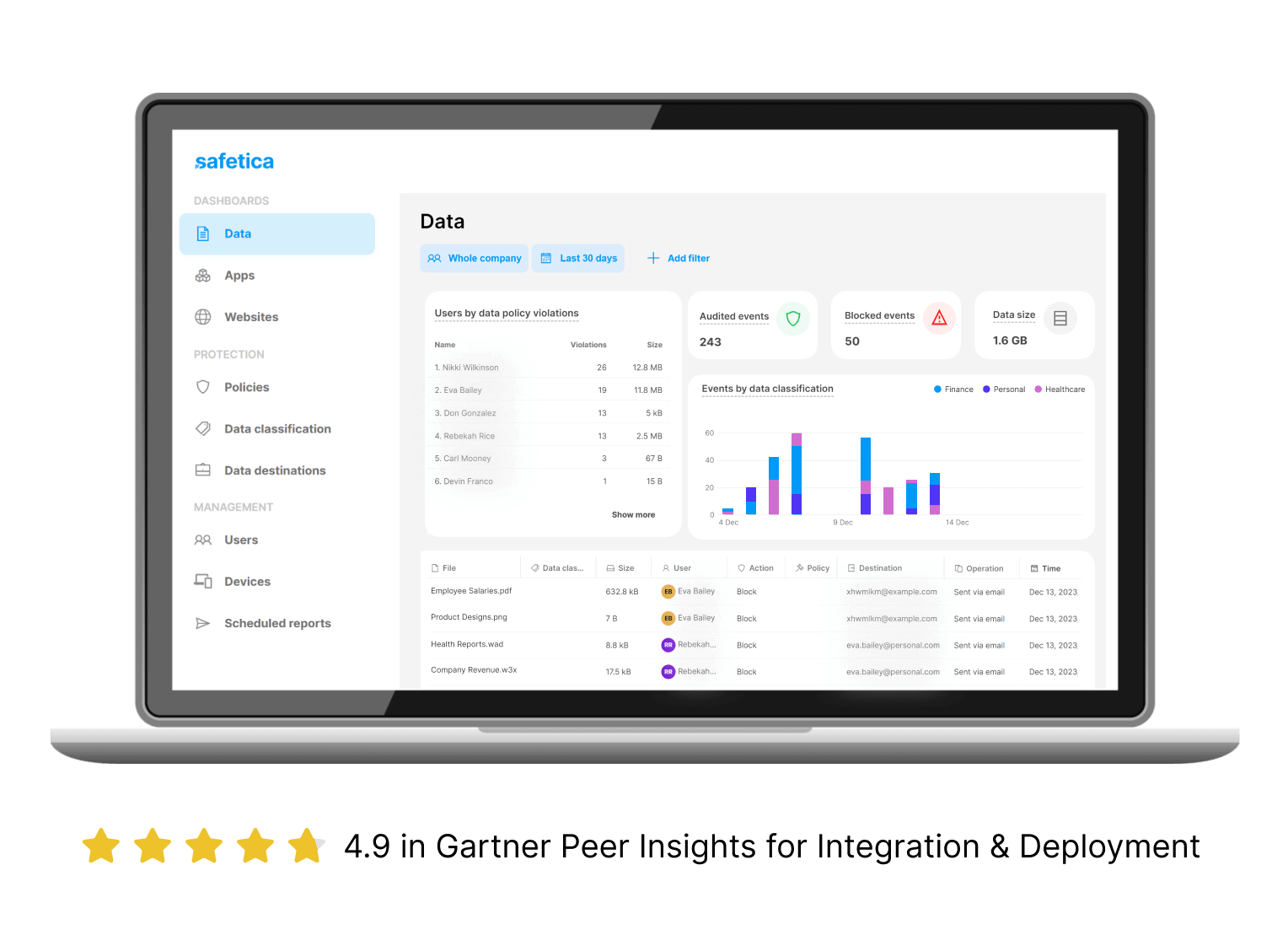
Safetica helps you to discover and classify valuable data using its unique Safetica Unified Classification which combines analysis of file content, file origin and file properties. It offers complete visibility and continuous monitoring, never missing a beat to instantly identify, classify, and track sensitive data.
Protect sensitive and business-critical data
With Safetica, you can protect sensitive business- or customer-related data, source codes, or blueprints from accidental or intentional leakage. It audits all sensitive data activities no matter where the data moves, so you can report and investigate where there’s a risk of leakage or theft.
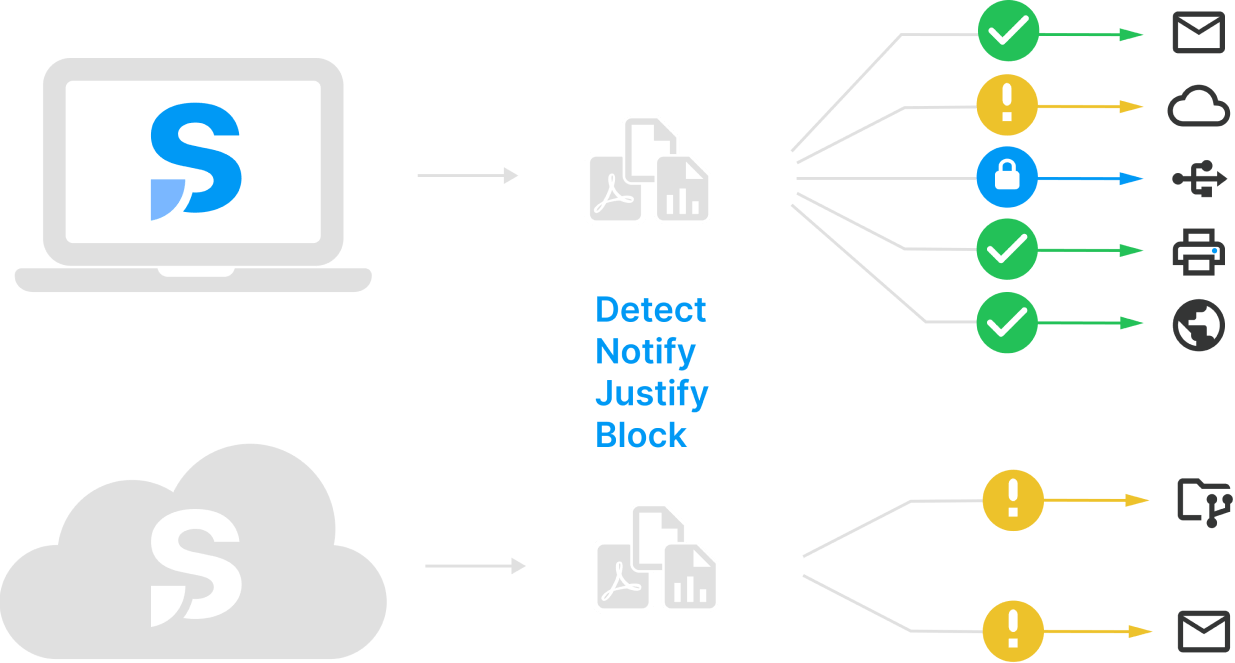
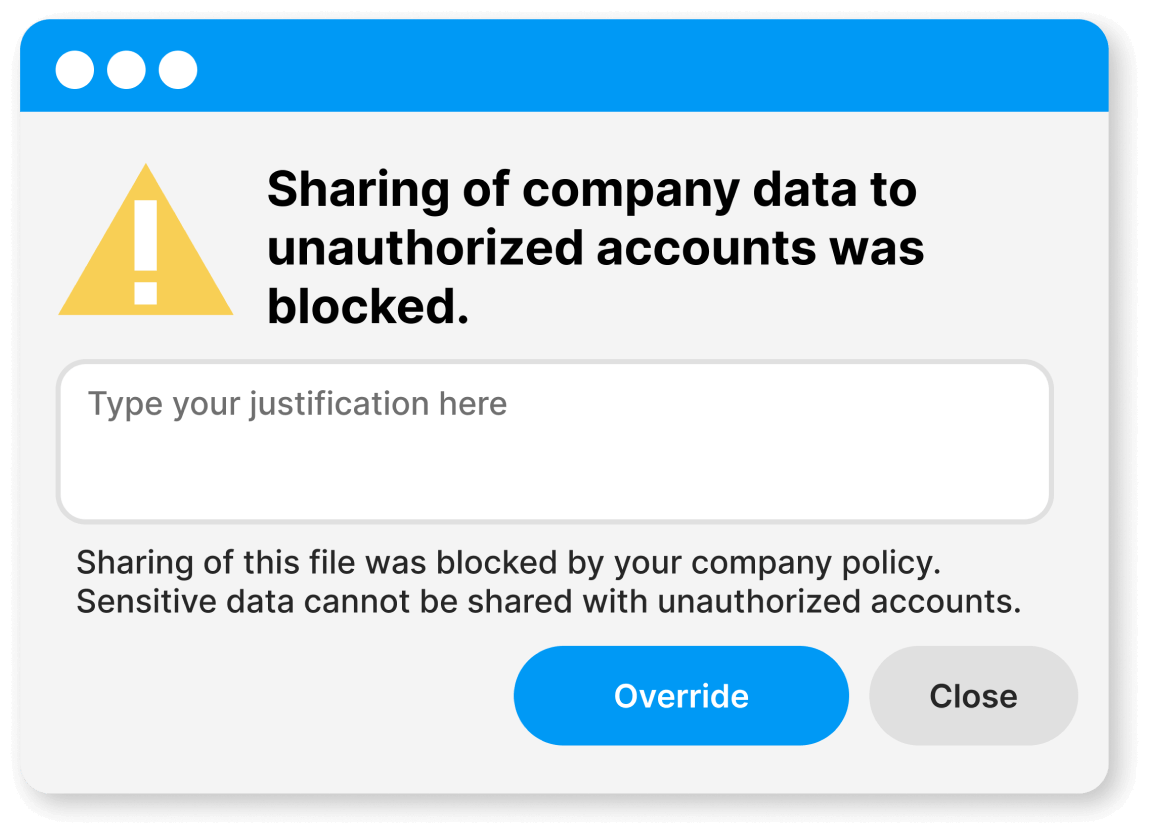
Empower users to work with sensitive data and promote security awareness
With Safetica, you can analyze insider risks, detect threats, and mitigate them swiftly. Notifications about how to treat sensitive data can help raise awareness around data security and educate your users.
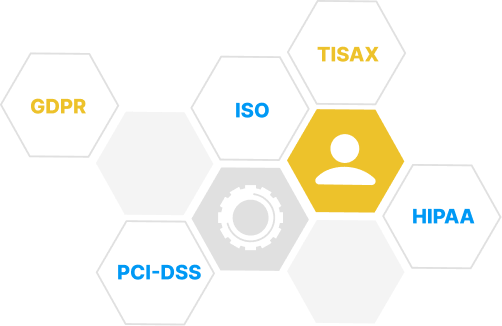
Detect and mitigate regulatory compliance violations
Safetica helps you to detect, prevent, and mitigate regulatory violations. Its audit capabilities support incident investigation to comply with regulations and data protection standards like GDPR, HIPAA, SOX, PCI-DSS, GLBA, ISO/IEC 27001, or CCPA.
Highly-rated by security admins for its product capabilities
Intuitive User Interface
Our Safetica console was designed with the user in mind. Navigate effortlessly through the system, empowering users to take control of their data security without extensive training.
Simplified Deployment Process
Flexible deployment options to businesses, with on-premise installation for maximum control and security, or cloud-based hosting for greater flexibility and scalability. You can count on our industry-leading partner and vendor support throughout the process.
Protection on Day One
Equipped with ready-to-use policies, allowing rapid implementation. Immediately and automatically detect and log incidents involving sensitive data, block risky applications and websites, and initiate universal monitoring.
Why Safetica
Continuous Monitoring and Auditing
Safetica offers real-time monitoring and audit trails that provide full visibility into data access and usage, supporting compliance and security efforts.
Zero-Day Threat Detection & Response
Safetica's proactive identification and immediate response to emerging threats ensure protection against zero-day vulnerabilities
Behavioral Analytics & Anomaly Detection
Safetica's advanced behavioral analytics identify suspicious activities and anomalies, enabling early detection and mitigation of potential security breaches.
Explore Beyond Data Loss Prevention
Know what sensitive data you have and where it is with DATA DISCOVERY AND DATA CLASSIFICATION
Secure, manage, and monitor USB and peripheral port to protect data with DEVICE CONTROL
Proactively identify anomalous activities and detect insider threats with INSIDER RISK MANAGEMENT
Ensure compliance with data protection standards and avoid costly penalties with REGULATORY COMPLIANCE
Analyze risk in user activities and block dangerous actions with USER ACTIVITY AND WORKSPACE AUDIT
Schedule a Demo
See how Safetica can disover, classify, and protect your most valuable data through a personalized demo.

